Encryption was once a luxury feature instead of a security requirement, however, as more and more users realize that they are walking with their mobile device loaded with personal data. Corporations and security-conscious individuals have started mandatory encryption policy, in order to prevent theft and loss of data, especially on airports where thousands of laptops are lost per year.
Windows 10 has followed the footsteps initiated by Windows 7 when it comes to hard drive encryption. Windows Bitlocker is available for all professionals using Windows 10 (Pro and Enterprise), which can be used in order to encrypt the information of the computer with the user’s password. It has been a very effective encryption tool without the hassle of downloading a 3rd party encryption software for the common Windows user.
It is, however, isn’t a perfect solution, in fact, encryption itself can lock the legitimate user out of their own files, if they end-up forgetting their password. Of course in a corporate environment, users are not signing-in using the local account set by Windows, but through a client-server system known as Active Directory. As part of this centralized system of User Account Management, decryption of BitLocker-protected drive can be easily be bypassed by system administrators if the BitLocker protection is tied into an Active Directory account (the desktop/laptop Windows PC is a member of the Domain).
But first, before proceed with the procedure of decrypting a previously encrypted Bitlocker drive using password reset for an Active Directory account, we will discuss a scenario where encryption cannot be reversed. This is when the Windows computer is not encrypted through normal means, but by a malicious process brought about by a ransomware virus.
Please make sure that the encrypted computer is actually locked-out by Microsoft Bitlocker, and not by malicious software. Once ransomware infects the machine, it will encrypt all the user files the local hard drive and USB-storage drives connected using a key. That same key is then uploaded to the command and control servers of the virus author, then the ransomware will prompt the user to pay for a certain amount in BTC (Bitcoin). There are basically two possible ways to reverse this damaging action of the ransomware, first is the non-recommended action, paying the ransom. This is a bad call for the user can do, as it further motivates ransomware authors to improve their current creations to become more profitable in the future.
The alternative is to fully reformat the hard drive, reinstall Windows and restore all the data files from the most recent backup. Yes, it is very inconvenient to do, but it is the only sure way to assure that the machine can be safely be used for corporate computing. If the hard drive is encrypted by Bitlocker, it is much easier to reverse the decryption, as Microsoft allowed password reset of Active Directory account.
The Steps Are:
- System administrator will login to the Windows Active Directory Server
- From the Windows Server desktop, open Active Directory Users and Computers. This can also be launched using the searchbox from the Start Menu.
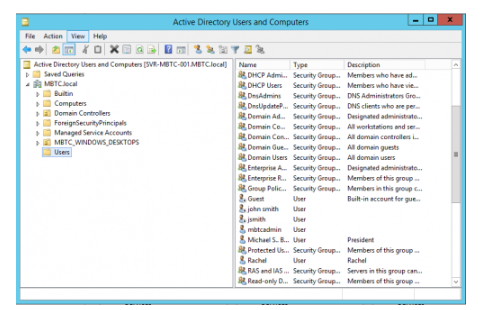
- In the Active Directory Users and Computers window, choose “Users” from the left pane.
- This should reveal the User Group categories on the right pane of the window.
- Double-click the User Group where the user account belongs, or if the user account is already showing from the initial Users subfolder, right-click the account and choose Reset Password…
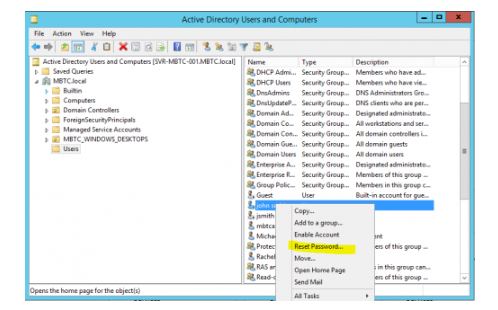
- The Reset Password dialogbox will open, type the chosen new password, then click the OK button.
- Open the laptop or desktop computer that was encrypted by Bitlocker. Make sure to connect to the LAN using a physical network cable instead of Wifi. While Windows is loading, it will automatically be queried by the Active Directory Server that the user has a password reset requirement. This enables the new password to be used on the previously locked-out machine.
