When reviewing their networks and PC installations for unchecked/overlooked attack surfaces, system administrators should always be alert. By definition, an attack surface is the area of a computer installation where an attacker can breach the system. For this reason, it is a critical job for system admins to maintain a computing environment with minimal attack surface.
One attack surface that is often overlooked is the Windows Remote Desktop (RDP) service. As a key part of account management, an IT team is expected to prioritize proactive maintenance of the RDP user list. So, while it is normal for workers to join and leave organizations at various points, user accounts with information on former employees are often not decommissioned fast enough, which makes them susceptible to breach. In fact, a black market for the sale of RDP user accounts has recently emerged, thereby expanding the profitability of cybercriminals beyond just virus development and cyberattacks.
This situation also generates more opportunities for attackers, as they are able to user servers as launching points for future cyber espionage and other nefarious actions. In a recent report, McAfee Advanced Research team revealed the black market for leaked RDP login credentials is growing. For example, one known place selling leaked RDP login credentials is the darknet website, Blackpass.bz—a highly lucrative black market business which features RDP login credentials being sold for less than $10.
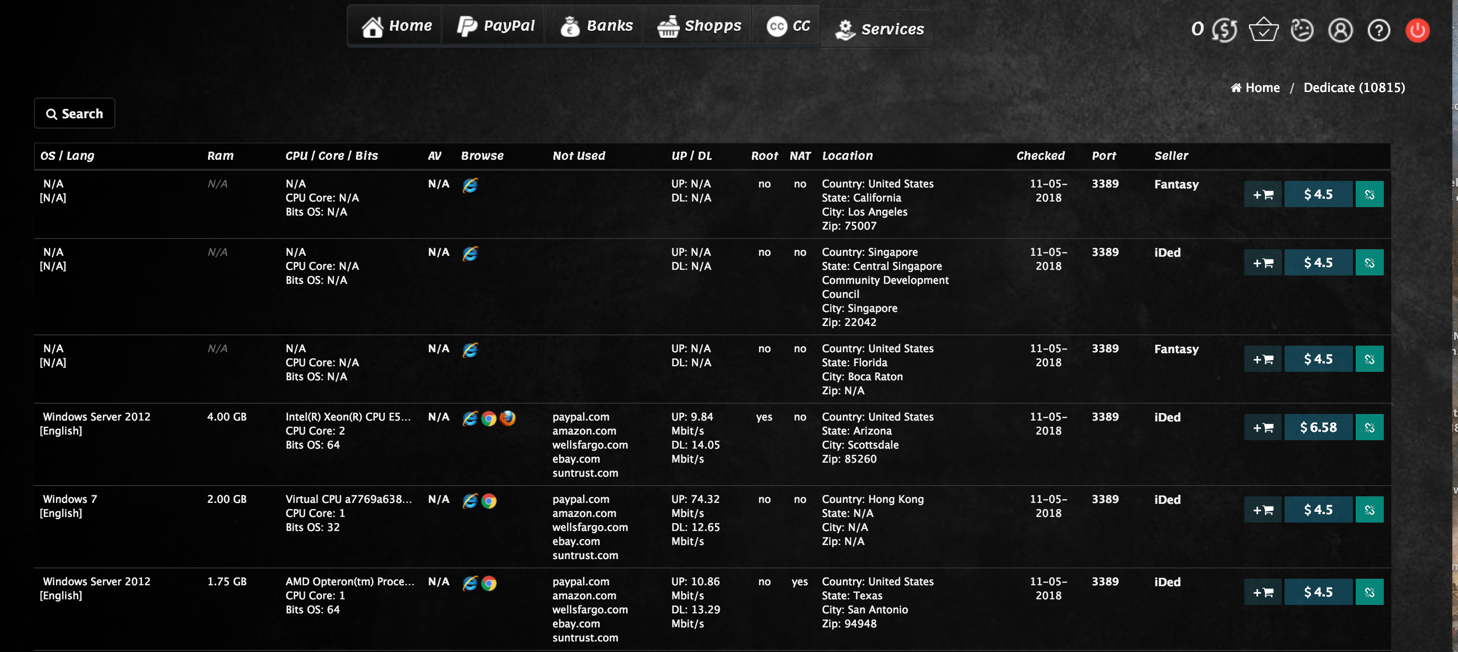
McAfee warns these black markets are not rare, a fact proven by the 40,000 RDP credentials now for sale at the Russia-based Ultimate Anonymity Service. Remote Desktop service is available with “Professional” and “Enterprise” versions of Windows XP through 10, and it is also supported and enabled by default in all versions of Windows 2003 Server, including newer ones. Given that many organizations use Windows as public digital bulletin boards, automated teller machines, and to assess point-of-sales, they all pose vulnerabilities for leaked RDP information.
Cybercriminals hijack servers and leak RDP credentials for these purposes:
- As a proxy machine for cyber attacks: This enables attackers to hide their point-of-origin by using the servers as a decoy. From the perspective of an investigator, the cyberattack looks like it came from an innocent server and not the real computer of the cybercriminal.
- As a launching platform for sending spam emails: If the servers are connected with an email system such as Exchange or Postfix, the cybercriminals can use it as a mass spamming machine.
- For illegal data mining: Hijacked servers often contain important personally identifiable data that can be sold to third-parties for a profit. This information can also be used for identity theft.
- For cryptocurrency mining: Hackers often use a server’s CPU resources to mine for cryptocurrencies like Bitcoin, Ether, and Monero. Being multicore processors, servers can provide decent gigahashes/second performance with crypto mining operations.
- As a launching platform for spreading ransomware: Using the network connections of the servers, the attacker can perform a vulnerability scan against the other computers on the network. This enables cybercriminals to use wormable ransomware to penetrate the rest of the network from the server.
System administrators are advised to perform the following actions, to prevent their servers from being exploited:
1. Strictly implement the company’s standard user account management. Immediately decommission any system access of employees as soon as they leave the organization.
2. Define user groups and access levels for each group. This can easily be accomplished using Windows Active Directory or Samba service in Linux. Users who don’t need remote desktop privileges should not have it by default. Perform regular audits of user groups to only include users that are authorized to connect via RDP.
3. Perform regular penetration testing drills against the network and computers. This can be done through the use of Kali Linux, a Linux distro specifically designed for penetration testing. Alternatively, the organization can hire an external ethical hacker to perform the penetration test on behalf of the company.
4. Invest in an intrusion detection system. This tool will monitor the entire network from unauthorized access at all hours of the day, all days of the week.
Related Resources:
Welcome To The Beauty And Horror Of The Dark Web
Ransomware For Sale On The Dark Web Is A Killer Bargain For Criminals
Security Tips Will Make You Bulletproof On The Dark Web
Stolen Facebook Accounts Now For Sale On The Dark Web
All You Need To Know About Gathering Intelligence On The Dark Web
