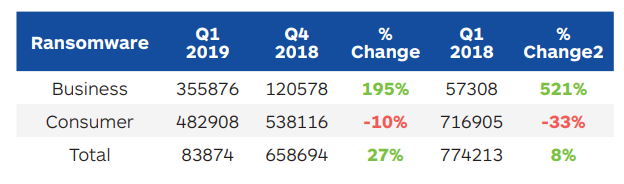
The system admins’ favorite antivirus program Malwarebytes has released the State of Malware Report covering the first quarter of 2019, highlighting the state of malware globally. The highlight of the report is the visible decreasing frequency of global ransomware infections, from 12 million incidents recorded in the first quarter of 2018 to just 4 million for the first 3-months of 2019. This is good news for everyone, but first looks alone can be deceiving. The consumer-side of the equation shows a significantly reduced case of ransomware infection compared to the same quarter last year, a reduction of 33%. This is a huge contrast to the enterprise ransomware infection rates which grew by 200% compared to the same quarter last year.
The below figure from Malwarebytes shows the huge contrast of ransomware infections between consumer devices and enterprise/corporate devices:
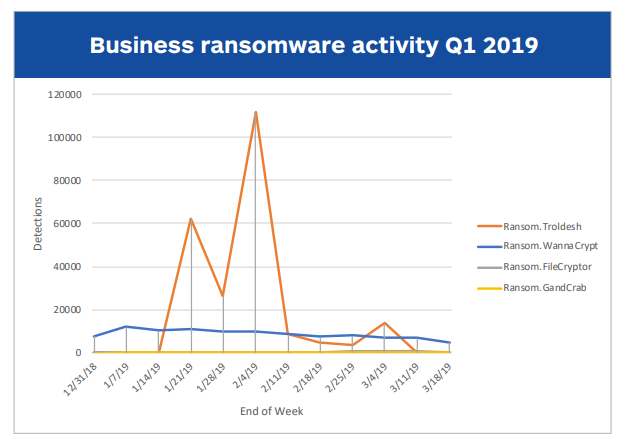
Malwarebytes blames the sharp increase of enterprise ransomware cases due to the proliferation of a ransomware named Troldesh. From all known ransomware, Troldesh infections grew by leaps and bounds which is not comparable with other ransomware that virtually maintained the same infection rates, unchanged for the first quarter of 2019.
“Despite this, the malware, most likely of Russian origin, still spiked in February 2019 via the crude delivery method of malspam attachment. It also required victims to open the ZIP file and run the JavaScript used to download the malware. Accompanying Troldesh’s ransom note were multiple text files to increase the likelihood of victims seeing one. The attack went after many file extensions and drives, whether fixed, remote, or removable,” explained in the report.
The graph below from Malwarebytes provides a virtual representation of the data collected by the antivirus telemetry when it comes to comparison of infection rates of Troldesh compared to more common ransomware in the wild like Gandcrab and Wanna Crypt.
Troldesh is considered a very old malware, with the earliest variant, detected as early as 2014. It continued to receive further enhancements from its authors, allegedly Russian nationals, it used the spamming campaigns which started in Feb 2019 to spread itself from mailbox to mailbox. Ransomware encrypts data, so if you don’t have a valid backup, it will be lost completely, the only way to recover it is to pay the ransom (although there’s no guarantee that you can recover the data once you’ve paid it). Some ransomware strain has also enhanced its ability to disable backups, including encrypting data on network drives. Ransomware has been reduced in number compared to one time, but now we aim to make it malicious to inflict fatal injuries, so we would like to make sure our backup system is complete.
However, globally speaking ransomware has lost the interest of malware authors to continue further research and development, as more profitable malware types such as banking trojans and cryptojacking virus. The Troldesh episode may only be a blip in the charts for the whole 2019, as it is not a very infection heavy malware compared to its cousins WannaCry (which still infects vulnerable computers today, even if its Command and Control Servers were already shut down) and the recently announced shutdown of GandCrab.
Related Resources:
