The reality of ransomware has skyrocketed in the past year, raking in millions upon millions of dollars for crafty hackers and their criminal syndicates, all of whom appear to have created the golden goose of malware. In a recent blog post, Sophos revealed that WannaCry’s spiritual successor, SamSam Ransomware, has now pulled in $5.9 million in profit.
The line chart below, which was released by Sophos, outlines the profit details of the incidents since SamSam was born. What’s most noticeable is the profitable trajectory the virus authors have enjoyed since it all began in 2016.
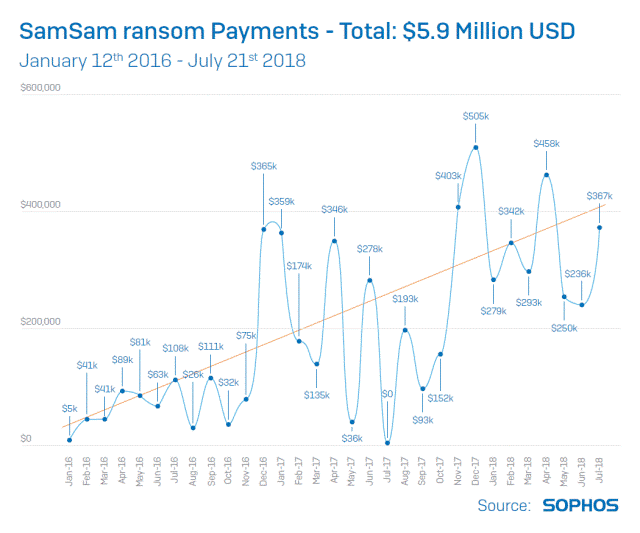
The report stated, “SamSam is actually deployed to computers on the victim’s network in the same way, and with the same tools, as legitimate software applications. Based on the known victims, it has been widely speculated until now that SamSam attacks are directed specifically at the healthcare, government, and education sectors. Sophos can confirm, this is not the case. The money trail also revealed that SamSam has netted nearly $6 million in ransom payments, about six times more than the most recent best estimate.”
Over time, SamSam variants gradually increase their ransom price in return for decrypting violated user data. What was once a $9,600 fee has since ballooned into a whopping $40,000 asking price. The report explains further, “If the SamSam attacker is on your network, they will likely stay on it until they succeed—unless of course, they are kicked off. Having gained access to a network, the SamSam operator uses a variety of tools to escalate their privileges to the level of Domain Admin. They can then scan the network for valuable targets and deploy and execute the malware as any self-respecting sysadmin might, using utilities such as PsExec or PaExec. Once it has been spread far and wide, multiple copies of the ransomware are triggered centrally and begin within seconds of each other. On each infected machine, files are encrypted in a way that is designed to maximize damage in the shortest amount of time.”
The new ransomware is more aggressive and focuses specifically on incurring the most damage possible against users. “Most ransomware is spread in large, noisy, and untargeted spam campaigns blasted out to thousands of people—sometimes even even hundreds of thousands. They use simple techniques to infect victims and raise money through large numbers of relatively small ransoms of perhaps a few hundred dollars each. However, SamSam is different—it’s used in targeted attacks by a skilled team or an individual who breaks into a victim’s network, surveils it, and then runs the malware manually. The attacks are tailored to cause maximum damage and ransom demands are measured in the tens of thousands of dollars,” the report concluded.
Although ransomware has been a highly profitable exploit for hackers, there seems to be a new form of attack on the horizon called crypto-jacking, and it is quickly taking the place of its more well-known predecessor. This new form of malicious software infects machines and forces them to mine for cryptocurrency using their own computer resources. Users usually have no idea the virus is running on their devices, although there are some signs of crypto-jacking like sluggish functionality and delayed response. All mining happens in the background while regular operations continue. Although crypto-jacking is still in its infancy, it current success bodes well for future exploits.
